网络拓补
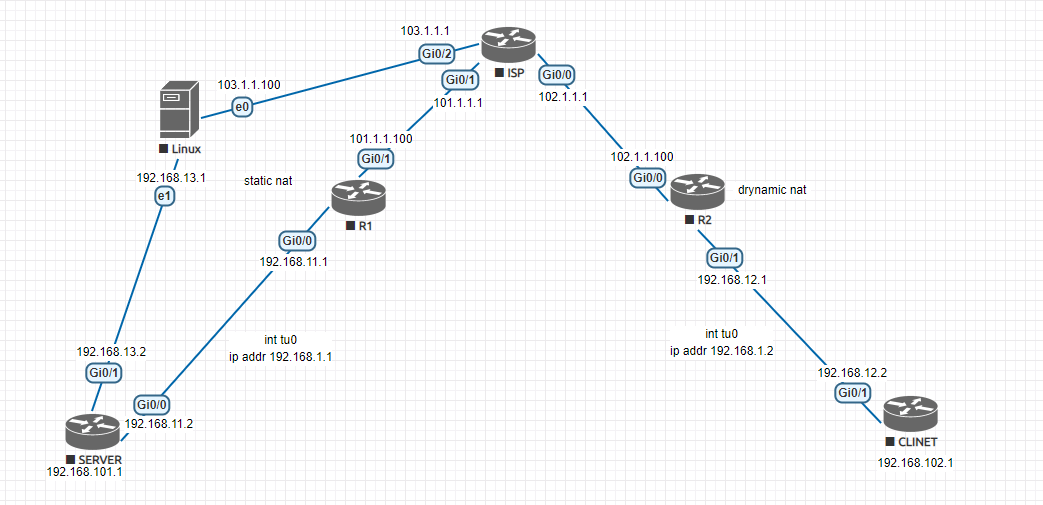
Server端的NAT分别用了Cisco与Linux来实现
配置
server
interface Loopback0
ip address 192.168.101.1 255.255.255.0
!
interface Tunnel0
ip address 192.168.1.1 255.255.255.0
no ip redirects
no ip next-hop-self eigrp 100
no ip split-horizon eigrp 100
ip nhrp authentication shiva
ip nhrp map multicast dynamic
ip nhrp network-id 1
ip nhrp holdtime 300
tunnel source GigabitEthernet0/0
tunnel mode gre multipoint
tunnel key 1
tunnel protection ipsec profile shiva
!
interface GigabitEthernet0/0
ip address 192.168.11.2 255.255.255.0
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/1
ip address 192.168.13.2 255.255.255.0
duplex auto
speed auto
media-type rj45
!
router eigrp 100
network 192.168.1.0
network 192.168.101.0
!
ip route 0.0.0.0 0.0.0.0 192.168.11.1
!
R1
interface GigabitEthernet0/0
ip address 192.168.11.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/1
ip address 101.1.1.100 255.255.255.0
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
!
ip nat inside source static 192.168.11.2 interface GigabitEthernet0/1
ip route 0.0.0.0 0.0.0.0 101.1.1.1
!
ISP
interface GigabitEthernet0/0
ip address 102.1.1.1 255.255.255.0
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/1
ip address 101.1.1.1 255.255.255.0
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/2
ip address 103.1.1.1 255.255.255.0
duplex auto
speed auto
media-type rj45
!
R2
interface GigabitEthernet0/0
ip address 102.1.1.100 255.255.255.0
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/1
ip address 192.168.12.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
!
ip nat pool test 102.1.1.200 102.1.1.210 netmask 255.255.255.0
ip nat inside source list natac1 pool test
ip route 0.0.0.0 0.0.0.0 102.1.1.1
!
ip access-list extended natacl
permit ip 192.168.12.0 0.0.0.255 any
!
CLIENT
crypto isakmp policy 1
encr aes
authentication pre-share
group 5
lifetime 1800
crypto isakmp key shiva address 0.0.0.0
!
crypto ipsec transform-set t-set esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile shiva
set transform-set t-set
!
interface Loopback0
ip address 192.168.102.1 255.255.255.0
!
interface Tunnel0
ip address 192.168.1.2 255.255.255.0
no ip redirects
ip nhrp authentication shiva
ip nhrp map 192.168.1.1 101.1.1.100
ip nhrp map multicast 101.1.1.100
ip nhrp network-id 1
ip nhrp holdtime 300
ip nhrp nhs 192.168.1.1
tunnel source GigabitEthernet0/1
tunnel mode gre multipoint
tunnel key 1
tunnel protection ipsec profile shiva
!
interface GigabitEthernet0/1
ip address 192.168.12.2 255.255.255.0
duplex auto
speed auto
media-type rj45
!
router eigrp 100
network 192.168.1.0
network 192.168.102.0
!
ip route 0.0.0.0 0.0.0.0 192.168.12.1
!
Linux
root@ubuntu:~# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:09:00:06:00 brd ff:ff:ff:ff:ff:ff
inet 103.1.1.100/24 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::250:9ff:fe00:600/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:09:00:06:01 brd ff:ff:ff:ff:ff:ff
inet 192.168.13.1/24 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::250:9ff:fe00:601/64 scope link
valid_lft forever preferred_lft forever
root@ubuntu:~# cat /etc/iptables/iptables.v4
# Generated by iptables-save v1.6.0 on Sun Sep 20 21:35:48 2020
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [160:9600]
:POSTROUTING ACCEPT [160:9600]
-A POSTROUTING -s 192.168.13.2/32 -o eth0 -j MASQUERADE
COMMIT
# Completed on Sun Sep 20 21:35:48 2020
# Generated by iptables-save v1.6.0 on Sun Sep 20 21:35:48 2020
*filter
:INPUT ACCEPT [1704:126220]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [1704:126220]
COMMIT
# Completed on Sun Sep 20 21:35:48 2020
root@ubuntu:~# iptables -vnL -t nat
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 240 packets, 14400 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 240 packets, 14400 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * eth0 192.168.13.2 0.0.0.0/0
root@ubuntu:~# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 0.0.0.0 0.0.0.0 U 0 0 0 eth0
103.1.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
192.168.13.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
实验结果
Server基于Cisco做NAT
检查
server#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 7/8/11 ms
server#ping 192.168.102.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.102.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 6/8/10 ms
server#show ip nhrp
192.168.1.2/32 via 192.168.1.2
Tunnel0 created 00:23:56, expire 00:04:34
Type: dynamic, Flags: unique registered used nhop
NBMA address: 102.1.1.200
(Claimed NBMA address: 192.168.12.2)
server#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is 192.168.11.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.11.1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
L 192.168.1.1/32 is directly connected, Tunnel0
192.168.11.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.11.0/24 is directly connected, GigabitEthernet0/0
L 192.168.11.2/32 is directly connected, GigabitEthernet0/0
192.168.13.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.13.0/24 is directly connected, GigabitEthernet0/1
L 192.168.13.2/32 is directly connected, GigabitEthernet0/1
192.168.101.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.101.0/24 is directly connected, Loopback0
L 192.168.101.1/32 is directly connected, Loopback0
D 192.168.102.0/24 [90/27008000] via 192.168.1.2, 00:21:18, Tunnel0
server#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 192.168.11.2
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.11.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (102.1.1.200/255.255.255.255/47/0)
current_peer 102.1.1.200 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 330, #pkts encrypt: 330, #pkts digest: 330
#pkts decaps: 333, #pkts decrypt: 333, #pkts verify: 333
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 192.168.11.2, remote crypto endpt.: 102.1.1.200
plaintext mtu 1426, path mtu 1472, ip mtu 1472, ip mtu idb Tunnel0
current outbound spi: 0x3CCC6D75(1020030325)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x496ECB4F(1231997775)
Server基于Linux做NAT
基于Linux的时候需要将server默认路由指向192.168.13.1,tunnel source 改为GigabitEthernet0/1,client端修改tunnel配置指向103.1.1.100
server(config)#no ip route 0.0.0.0 0.0.0.0 192.168.11.1
server(config)#ip route 0.0.0.0 0.0.0.0 192.168.13.1
server(config)#interface Tunnel0
server(config-if)#tunnel source GigabitEthernet0/1
client(config)#interface Tunnel0
client(config-if)#ip nhrp map 192.168.1.1 103.1.1.100
client(config-if)#no ip nhrp map multicast 101.1.1.100
client(config-if)#ip nhrp map multicast 103.1.1.100
检查
server#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 7/7/8 ms
server#ping 192.168.102.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.102.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/5 ms
server#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is 192.168.13.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.13.1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
L 192.168.1.1/32 is directly connected, Tunnel0
192.168.11.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.11.0/24 is directly connected, GigabitEthernet0/0
L 192.168.11.2/32 is directly connected, GigabitEthernet0/0
192.168.13.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.13.0/24 is directly connected, GigabitEthernet0/1
L 192.168.13.2/32 is directly connected, GigabitEthernet0/1
192.168.101.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.101.0/24 is directly connected, Loopback0
L 192.168.101.1/32 is directly connected, Loopback0
D 192.168.102.0/24 [90/27008000] via 192.168.1.2, 00:08:40, Tunnel0
server#show ip nhrp
192.168.1.2/32 via 192.168.1.2
Tunnel0 created 00:08:31, expire 00:03:54
Type: dynamic, Flags: unique registered used nhop
NBMA address: 102.1.1.200
(Claimed NBMA address: 192.168.12.2)
server#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 192.168.13.2
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.13.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (102.1.1.200/255.255.255.255/47/0)
current_peer 102.1.1.200 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 115, #pkts encrypt: 115, #pkts digest: 115
#pkts decaps: 96, #pkts decrypt: 96, #pkts verify: 96
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 192.168.13.2, remote crypto endpt.: 102.1.1.200
plaintext mtu 1426, path mtu 1472, ip mtu 1472, ip mtu idb Tunnel0
current outbound spi: 0xAE5EB92F(2925443375)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x729043BB(1922057147)
转载请注明来源
